
With the global cost of cybercrimes running into the billions, an SEC investigative report on cyber-related frauds from October 2018 presented a clear warning to public companies: revisit the effectiveness of your IT internal controls to guard against business email compromises (BECs) and other emerging cyberthreats.
Below, we outline three risk factors impacting financial reporting and five steps your organization can take to counter them.
SEC Regulatory History Overview
The SEC requires issuers to keep accurate books, records, and accounts, as well as maintain a system of internal controls and compliance procedures to ensure investors can make informed decisions.
The SEC has long held an interest in the books and records provisions of bills Congress passes including the 1934 Exchange Act, the 1977 Foreign Corrupt Practices Act (FCPA), and more recently, the Sarbanes-Oxley (SOX 404) Act of 2002.
The SEC linked accurate books and records to international bribery with the FCPA and internal controls over financial reporting (ICFR) with SOX 404. In its October 2018 report, the SEC linked the books and records to mutating cyberattacks. This, however, is new.
Takeaways from SEC Report on Cyber-Related Frauds
In its 2018 report, the SEC described the increase in cyber-related attacks targeting public companies and the role internal control requirements played in the success or failure of those attacks. The SEC cited BECs as the fastest growing attack vector.
Losses from BECs in 2019 exceeded $26 billion, and they’re increasing at a rate of more than 200% per year.
While the exponential increase in BECs is a new data point, the SEC’s expectations remain the same as it relates to evolving threats: organizations should regularly review and update controls to address changing risks.
The SEC communicated that it expects issuers to include cyberthreats in their SOX risk assessments.
The exponential increase in BECs and other cyberbreaches described in its 2018 report prompted the SEC to again consider increasing enforcement activity for the books and records provision because of the overlap between IT controls and financial reporting.
To date, however, the SEC has focused its cyber enforcement actions on the accuracy of the issuer’s disclosure and characterization of material cyberbreaches. Whether you work in a public or private company, their report serves as a warning: companies should update their IT risk assessment and enhance their internal controls to protect their financial and data assets.
To develop a tailored IT risk mitigation plan, it’s important to understand three trends in IT risk impacting financial reporting.
3 IT Risks Impacting Financial Reporting
The current IT risk environment operates under a heightened state of awareness. If left unaddressed, IT risks can leave companies exposed and vulnerable to costly attacks, both monetarily and in reputation.
Technology Proliferation and Digitization
Virtually all business transactions today transpire through technology or email. Since the COVID-19 pandemic began, many companies digitized their businesses even faster than before. While digitization increases profits, it also increases vulnerability to cyberattacks.
Regulation Changes and Their Impact on IT Controls
The SEC allows nonaccelerated filers with annual revenues of less than $100 million and a public float of less than $700 million to skip section 404(b) of the SOX, which requires a publicly held company’s auditor to attest to—and report on—management’s assessment of its internal controls.
The SEC gave nonaccelerated filers the choice of undergoing a 404(b) audit so that businesses could avoid auditing fees and spend more on hiring or investing in research and development (R&D).
University studies, however, have shown that shareholder benefits of the 404(b) audits outweigh the costs incurred for the 358 companies that would’ve been exempted.
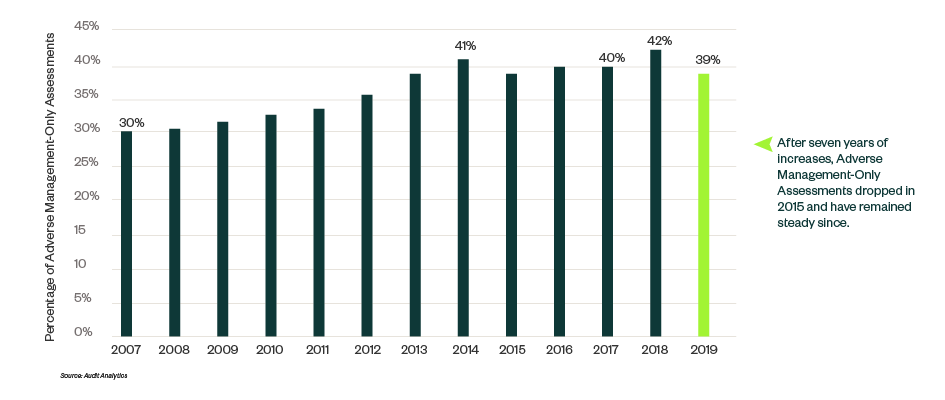
Reports show that the statistical probability of having an Adverse Management-Only Assessment over internal controls increases to nearly 39%, because external auditor and internal auditor coaching, assessing, and testing of controls is minimal.
Like people, companies with coaching and training perform better. Without 404(b), internal control issues metastasize and grow because no one audits the veracity of the Management-Only Assessment.
Shortages of IT Risk and Compliance Talent
Earlier this year, Harvard Business Review released a study entitled 9 Trends That Will Shape Work in 2021 and Beyond which concluded that companies will look to rent talent to fill the skills gap.
The number of skills companies search for has risen dramatically and organizations can’t reskill the capabilities of their existing workforce fast enough to meet their changing needs.
The impact of the talent shortage revealed itself because most organizations don’t update their IT risk assessments annually.
On top of talent shortages, cost concerns and general denial of risk contribute to factors which keep IT risk assessment from working as it should.
5 Steps to Counter IT Risks
Fortunately, it’s not too late to assess your IT risk and design and implement controls to protect your company.
Take the following steps to assess your standing:
- Create, develop, and deploy IT risk training across the organization. In addition, work to curate additional modules for leadership and IT compliance professionals.
- Develop cybersecurity policies and understand their intersection with SOX. Assess how cybercontrols relate to the effective operation of automated controls, the accuracy and completeness of key reports, and disclosure controls over material cyberbreaches.
- Update IT risk assessment annually and implement controls as necessary. Driving growth requires taking steps to digitize and introduce new technologies, but companies also must keep technology risk in mind to identify and address mutating cyberthreats.
- Identify key controls and data analytic tools that prevent potential illegitimate disbursements. Monitor and update controls for new cyber variants, systems changes, and systems upgrades.
- Regularly evaluate the design and test operating effectiveness of five key IT general controls. These controls include multifactor authentication, segmented critical data, network scans, limited super user access, and up-to-date patches.
Additional Tips to Stay Ahead of Risks
Most companies understand what they need to do. Taking action, however, requires discipline and determination.
While many companies may defer their maintenance in SOX controls, performance-minded companies take the five steps above to minimize the cost of cyber insurance and the probability of an adverse SOX assessment, and avoid crippling cyberattacks.
Get started now by meeting with your business advisor to discuss:
- Results of your most recent IT and cyber-risk assessment
- Any identifiable IT control gaps
- Whether your external auditor relies on controls in its audit approach
- How your employees who would benefit most from IT risk assessment training
We’re Here to Help
If you have any questions regarding your IT risk or internal controls, please contact your Moss Adams professional.