
Vulnerabilities in the transportation and logistics industry make prime targets for exploitation due to the high value of transactional data, personally identifiable meta data, and proprietary data that supports the complex network of logistics.
In recent years, the United States has seen a steady rise in the number of cyberattacks and ransoms demanded by hackers. Ransomware is a form of malicious software that infiltrates a computer or network and limits or restricts access to critical data by encrypting files until a victim pays ransom often through untraceable cryptocurrency.
The value of confidential data, and by extension, the extraordinary amount of information humans and machines exchange, shouldn’t surprise organizations that support transportation. However, the risk tolerance of data integrity and data loss prevention falls at the mercy of a balancing act between organizational resources and the potential for irreparable damage to transportation organization customer bases.
What Is a Subservice Organization?
The American Institute of Certified Public Accountants (AICPA) defines a subservice organization as a service organization used by another service organization to perform some of the services provided to user entities that are likely to be relevant to those user entities’ internal controls over financial reporting (ICFR).
In today’s business environment, an organization typically outsources certain functions to third parties—service organizations—that may in turn outsource certain functions to subservice organizations. Unfortunately, this can unknowingly leave the organization’s transactional or confidential information at risk.
The Transactional Information Cycle
Entities participating in the transportation and logistics industry as a subservice organization have a Transactional Information Cycle which the data goes through.
The stages within the Transactional Information Cycle include:
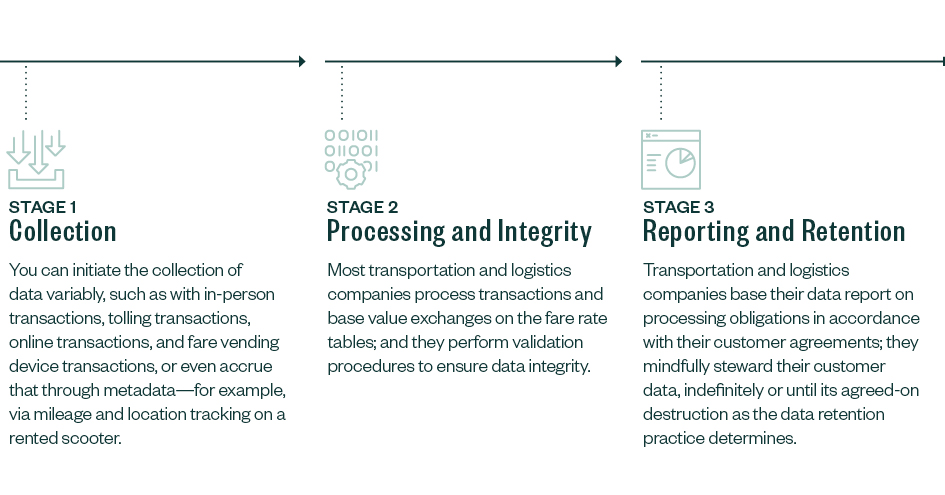
Transportation subservice organizations face two significant transactional information challenges of data integrity and data loss prevention.
Data Integrity
It can be a challenge to maintain accuracy and completeness of data.
Accuracy
After a transaction, IT systems ensure that the transaction matches the dollar amount recorded in the organization’s records. Automation and configurations hold the quality of data validation and integrity checks to a standard with no room for error.
Improper configurations could impact a significant amount of transactions before someone flags the issue and enacts an emergency change, leading to both a financial impact and a loss of customer confidence.
Completeness
Improper configurations or unapproved changes to a transaction system rate table can create incomplete or inaccurate results, potentially impacting financial reporting.
A transportation subservice organization without a mature change management process leaves itself vulnerable to unauthorized code or configurations in the transaction calculation process, affecting all customer transactions.
Data Loss Prevention
It can be a challenge to protect the transactional data from unintended loss or use.
Once a transaction occurs existing secured systems and service organization controls should protect the data and prevent unauthorized access. For example, you could categorize and restrict customer information based on a data classification. Manual processing of data introduces the risk of error into the equation if no one properly classifies, processes, retains, or disposes of system data.
Customer and proprietary data, containing personally identifiable information (PII), and customer traveling habits, make it crucial for transportation subservice organizations to have adequate security awareness training along with enforcement.
A data breach, the most common type of incident, presents the risk of proprietary data loss and threatens the organization’s competitive advantage. While organizations can’t predict when a data breach will impact them or the scope of the attack, preventative measures can help avoid disruption to business operations.
Reducing and Managing Risks
Before developing a plan to manage risk, organizations should first properly analyze and triage current risks. They should also ensure they’re either accepted risks of doing business or sufficiently mitigated through your company’s control framework and application.
Conducting annual risk assessments, at a minimum, along with creating and updating a risk framework represent fundamental steps towards understanding the risk environment in a transportation subservice organization. In short, a properly designed and functioning set of controls can help an organization address risks, prevent issues before they arise, and mitigate costly consequences.
SOC Examination
When you outsource functions to third parties, you assume their risk profile. A user entity outsources functions that affect its ICFR. Management of the user entity needs to gain an understanding of the design and operating effectiveness of certain controls that the service organization performs. Generally, a system and organization control (SOC) examination accomplishes this.
A SOC examination reports on the effectiveness of an organization’s internal controls and safeguards that they have in place while providing independent and actionable feedback. Financial statement auditors may use them to help reduce audit procedures, and sophisticated users of service organizations push for them to ensure secure systems and protected data.
The benefits of a proactive risk mitigation strategy far exceed the damage a reactive approach to risk management can cause, especially when data loss can cost millions, erode decades of brand equity, and bring daily operations to a halt.
We’re Here to Help
To learn more about SOC examinations and IT controls to protect your organization, contact your Moss Adams professional.
You can also learn more about our Transportations & Logistics Practice and additional topics affecting the industry.