
The term zero trust has become common for highly secure systems that function under the precept that access always presents a risk. While many understand the basic concept of zero-trust architectures, few understand the details.
Below is a review of not only what a zero-trust framework entails, but how zero-trust architectures satisfy the security principles contained within the National Institute of Standards and Technology (NIST) cybersecurity framework—an industry standard to some extent, though one of many possible frameworks.
What Is Zero Trust?
Zero trust secures an organization by eliminating the implicit trust that many systems have. For example, it’s common to be able to access systems without logging in when inside the network as opposed to a zero-trust framework that would require continuous validation at every stage of any digital interaction.
Rooted in the principle of never trust, always verify, zero-trust security is designed to protect digital environments by incorporating the following.
- Strong authentication methods
- Leverage network segmentation
- Prevent lateral movement
- Provide Layer 7 threat prevention
- Simplify least access policies
A zero-trust architecture can analyze multiple attributes to authenticate system access, including location, the user’s role within an organization, common access times, and the overall health of the system.
Origins of Zero Trust Architecture
Zero trust is based on a set of guiding principles that evolved from static access control policies, which allowed permissions to a user until the user logged out, into more dynamic policies with multiple factors, that may, for example, kick users off the system before they initiate their own logout. The adoption of zero trust architecture is a response to recent trends of remote users, bring your own devices (BYOD), and cloud-based assets.
Key Concepts of Zero Trust Security
One key idea of zero trust security is that trust and safety can’t be based on physical location or access to a network. Trust must be evaluated on a per-transaction basis. According to Microsoft, “Zero trust is the essential security strategy for today’s reality.”
All hosts, applications, users, and devices are considered internet-facing, receiving the same security treatment afforded to web applications. This is achieved in part by mitigating the effects of lost or stolen credentials, which can be done by considering both the user and the device when determining trust or privilege.
Trust Controls
Granting trust can be more granular than binary. Attribute-based access controls (ABAC) can consider multiple attributes such as temporal, geographic, or even behavioral attributes.
For example, access to an application by a user from their normal location during working hours could be granted, but access from a new location or during different hours would require an additional authentication factor.
Zero Trust Policy Engine
The policy engine is the executive function at the core of a zero-trust architecture, providing the ability to dynamically adjust policies and access, which makes zero trust networks able to respond autonomously to known and unknown attacks by malicious actors.
The policy engine, or control plane, will control what can be accessed in the data plane and is aided by the principles of automation, encryption, least-privilege, and time-boxing.
Tenets of Zero-Trust Security
Below are the summarized tenets of zero trust architecture as defined by NIST800-207.
- Resources can include users, data sources, devices, services.
- All communication is secured.
- Asset security or patch level factors into the access-granting decision.
- Authentication and authorization are based on dynamic policies.
- Continuously learn and improve security posture by collecting data such as asset security state, access requests, network traffic, etc.
The zero trust architecture tenets dictate that access is:
- Granted per session with the least access privilege
- Granted to each resource irrespective to access to another
- Driven by dynamic policies based on attributes that an organization assigns to a user, data asset, or application
NIST Cybersecurity Framework
How do the principles of zero-trust security align with an established security framework, such as the NIST cybersecurity framework?
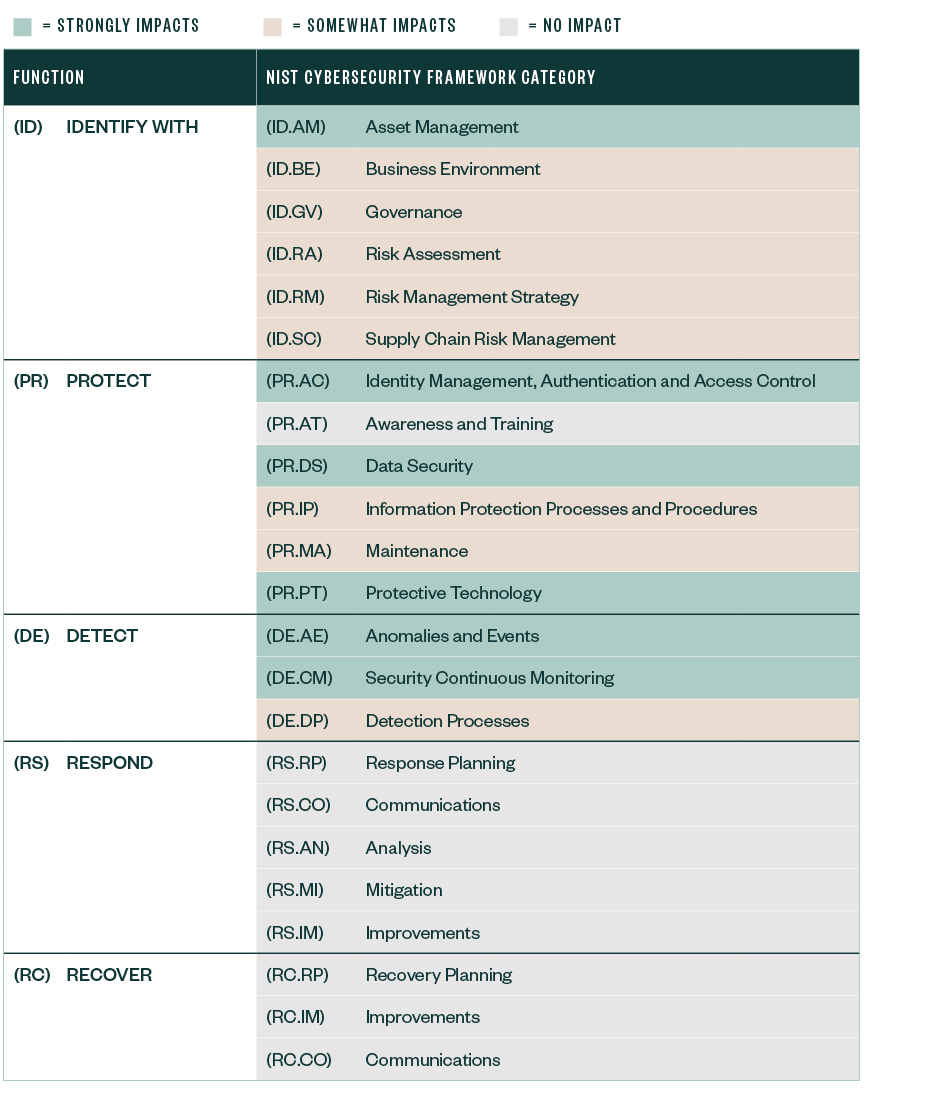
With the zero-trust focus on identifying resources, trust, and opportunities to improve security through monitoring, zero trust appears to be making a positive impact on the NIST Cybersecurity Framework Category functions of identify, protect, and detect. While zero trust architecture likely won’t affect existing processes related to the NIST cybersecurity framework functions of respond and recover, zero trust’s focus on limiting lateral and east-west movement through a network should greatly decrease the amount of respond and recover work required.
NIST Cybersecurity Framework Categories
Explore the below table for the NIST cybersecurity framework categories that measures the impact a zero-trust framework would have on listed functions where zero trust strongly impacts (green), zero trust somewhat impacts (beige), and zero trust either doesn’t impact or doesn’t apply (gray).
Zero Trust Security Threats
Zero trust may be an essential security strategy for today’s dynamic security landscape, but it also comes with some inherent risks, such as the following.
- Compromise of underlying trust algorithm or decision process via unapproved changes, genuine mistakes, or intentional manipulation of the non-human aspects of the algorithm
- Denied access to the decision process due to a denial-of-service attack or some other network disruption
- Vendor lock-in due to proprietary data formats
Zero Trust Roadmap
Moving to zero-trust security should be viewed as a long-term strategy. Different architectural approaches to implement a zero-trust architecture include the following.
- Identity-driven attributes to determine application access
- Controlled access to network micro-segments
- Dynamic network infrastructure through software-defined perimeters
Architectural Approach
Zero trust architecture architectural approaches can be deployed via the following.
- Agents
- Gateways
- Enclave-based
- Portal-based
- Application sandboxing
Ask These Questions to Prepare Your Zero-Trust Security
Answering these questions will help in considering a zero-trust security solution for your organization:
- Does it require installing an agent on the client?
- Does it only work in the cloud or on-premises?
- Does it log interactions for analysis?
- Does it support different applications, services, and protocols such as web, secure shell, internet protocols, and so forth?
- Does it require users to change their behavior?
Regardless of the approach used to deploy a zero-trust architecture, organizations must plan to refine their trust algorithms with the following baseline factors:
- Assets
- Users
- Business processes
- Traffic flows
- Dependency mappings
Some recommendations include starting with a low-risk business process to limit the impact of potential disruptions and operating in report-only mode to allow iterating and refinement.
Next Steps
Many vendors offer solutions to help organizations move toward zero-trust frameworks, but those solutions require a consistent high level of commitment from organizations.
Once those baselines are established and added to the policy engine, many solutions allow companies to run zero trust alongside their current environment or they may require a switch, either abruptly or over time. While the goal is to have zero-trust security in place for the entire environment, it’s not unusual for organizations to introduce zero-trust architecture in a phased approach.
We’re Here to Help
A zero-trust architecture can be the next step in your cybersecurity long-term plan. Explore our cybersecurity resources to expand on your approach and system options. If you have questions about zero trust security implementation, reach out to your Moss Adams professional.