The HITRUST CSF is a certifiable security and privacy framework that helps organizations secure, comply, and assess against several security and privacy-related standards, regulations, and recommended practices.
HITRUST is used by organizations in many different highly regulated industries, such as health care organizations, technology companies, insurance plan providers, and any organization that handles different classifications of sensitive data.
With its version 11 update, HITRUST has maintained its commitment to improve the framework. The latest version helps organizations better manage risk by staying updated on the current cyberthreat landscape.
HITRUST CSF Version 11
HITRUST launched version 11 of the CSF at the beginning of 2023.
HITRUST is decommissioning the version 9.x series. Organizations currently using version 9.1 through 9.4 must switch over to version 11 or a higher version of 9.x—either 9.5 or 9.6—by 2024.
Timing and Deadlines
Organizations have until December 31, 2024, to submit assessments using versions 9.1 through 9.4, but any new assessment objects using these versions had to be created by September 30, 2023.
Organizations currently using versions 9.5 or 9.6 for r2 assessments can continue to use those versions, but they will also be decommissioned in the future.
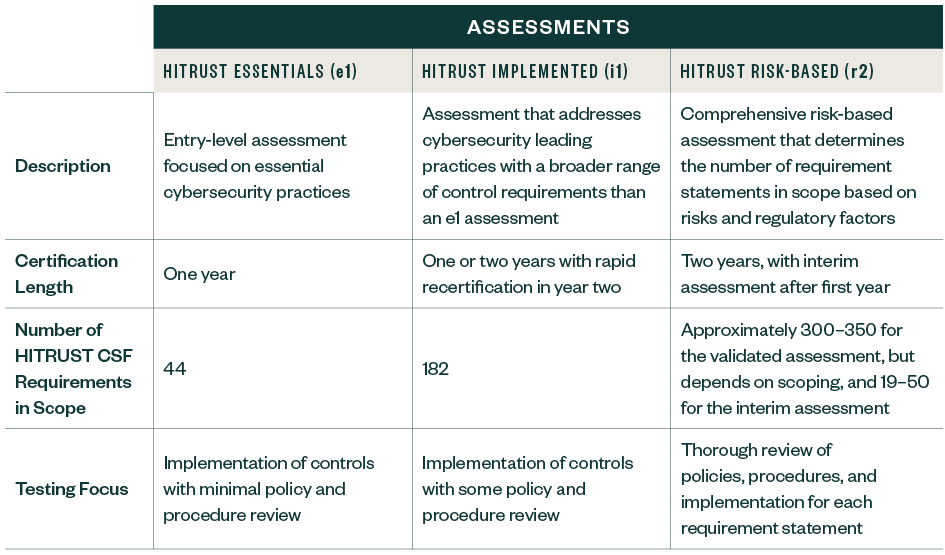
Three HITRUST Certification Assessment Types
The following is a cursory explanation of each assessment type. For more details on each assessment, visit HITRUST Assurance Advisories.