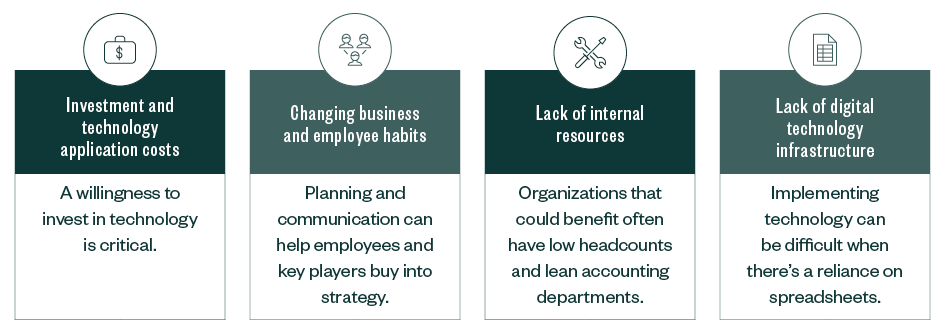
Digital Transformation Strategy Challenges
Internal Processes and Controls
In advanced technological environments, organizations can more reliably and consistently address risk if they can move to a more automated solution. IT-driven controls aren’t subject to human error, bias, or management override.
Companies can use the following controls to assist in their accounting.
Manual Controls
Though technology can be used to supplement manual controls, there will always be instances where management will need to make a subjective conclusion on a complex topic. This must be done via some type of human intervention.
Consider manually monitoring the following:
- Management review controls (MRCs)
- Estimates or accruals and other dissemination of critical information
- R&D spend expectations and percentage complete
- Vendor banking details
Spreadsheets and End-User Controls (EUCs)
In spreadsheet-heavy environments, organizations can establish entity-wide programs to help manage EUCs.
The following are strategies to implement that support security if your organization uses spreadsheets:
- Maintain accurate inventory of all discovered, registered, and managed files
- Implement version, access, change, and data integrity controls
- Establish procedures that monitor changes to inputs and logic
- Restrict access to spreadsheets so that only supervisors have access to unlock cells
- Leverage Excel add-ons and embedded applications, such as Smartsheet, Tableau, or Domo
IT Application Controls (ITACs)
ITACs include safeguards in relation to specific applications. ITACs prevent, detect, and correct transaction errors and fraud in application programs. They are concerned with the accuracy, completeness, validity, and authorization of the data captured, stored, transmitted to other systems, and reported.
Several types of application controls exist with the objective to ensure that input and output data are accurate and complete, processed in an acceptable time, and a record is maintained to track the process of data from input to storage and to the eventual output.
Examples of application controls are:
- Ensuring goods and services are only procured with an approved purchase order
- Monitoring segregation of duties based on defined job responsibilities
- Identifying received goods and services are accurate upon receipt
- Ensuring fixed-asset depreciation is recorded accurately in the appropriate accounting period
- Determining whether there’s a three-way match among the purchase order, receiver, and vendor invoice
IT General Controls (ITGCs)
ITGCs refer to the overarching controls that relate to security, change management, and the use or design of computer programs. They ensure an organization’s control environment is stable and well-managed, including the IT infrastructure and software acquisition, development, and maintenance.
Several types of ITGCs exist with the objective to ensure that system and organization controls (SOC) reports for cloud-based systems are assessed for unmitigated risks, security and access to systems and key reports are limited via least privilege, and there is control over batch processing.
Managing third-party risk is critical for companies that rely heavily on third parties. Are you outsourcing IT or R&D? If so, work with vendors who have current SOC reports.
Organizations can gain significant effectiveness and efficiency in maintaining internal controls over financial reporting by following the steps needed to maintain this strong IT general control environment.
Automated Workflows
To further strengthen your internal processes and controls, you can utilize automated process workflows.
Examples of automated process workflows include:
- Journal entry approval
- New vendor approval
- Vendor bill approval
- Vendor payment
- Purchase order and purchase request
Defining Scripts
Gain some efficiency and effectiveness in your operations using scripts. A script is a program or sequence of instructions that takes a series of commands and turns it into a single command. With one click, the script can run several sequential tasks.
A common example is using scripts for payroll processes.
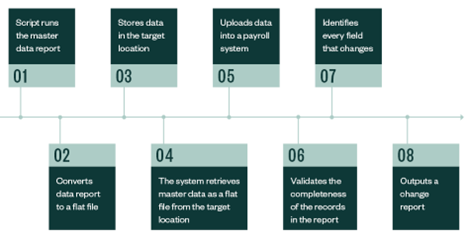
There are many individual activities during this process, but with a script, the system is programmed to run the activities consistently and without error.
The script will let the user know if an error occurs. Scripts can be a very potent and effective tool for increasing the effectiveness and efficiency of your operations.
We’re Here to Help
For guidance on creating and implementing a digital transformation strategy, contact your Moss Adams professional.


